please add support for SRI sub resource integrity hashes
Any updates? Does Matomo now support SRI?
Hi,
Can you further explain in which context you would like Matomo to utilize SRI hashes?
I have a website that has tracking code of Matomo.
In my nginx config, I have something like:
add_header Content-Security-Policy "default-src 'none'; script-src 'sha256-abcd'; object-src 'none'; require-sri-for script; base-uri 'self'; frame-ancestors 'none'; form-action 'none'; block-all-mixed-content";
CSP for Matomo is explained on Matomo FAQ.
I generate a hash for the matomo.js of my instance on: Report URI: CSP Hash Generator
And on my index.html, I have also: <script src="https://matomo.example.com/matomo.js" integrity="sha256-abcd=" async defer></script>.
Matomo should:
- generate and serve tracking.js file from Matomo instance for each website it is analysing ;
- serving from the start CSP-compatible tracking code
- provide the SRI hashes for scripts matomo.js & tracking.js to be able to add quickly the hashes to the tracked web pages and to the server config header line for both Apache & Nginx
But this would mean that you could never update Matomo or any plugin that changes the tracking as this would change the matomo.js file.
If Matomo is updated, and matomo.js with it, the new integrity hash for matomo.js will be provided by Matomo instance on the webapp, and eventually by email notification?
Hi,
If manually updating the tracking code is okay for you, then it should be already possible to build a plugin that does this.
Plugins can modify the tracking code Matomo displays (to add a SRI line), can read the file to generate the right hash and (untested) should have some way to find out when this file changed to create a notification.
if a site has CSP with require-sri-for script and style, how and where do i specify an integrity hash for the piwik.js?
ie.
<!-- Matomo -->
<script type="text/javascript">
var _paq = _paq || [];
/* tracker methods like "setCustomDimension" should be called before "trackPageView" */
_paq.push(["setDocumentTitle", document.domain + "/" + document.title]);
_paq.push(["setCookieDomain", "*.example.org"]);
_paq.push(["setDomains", ["*.example.org"]);
_paq.push(['trackPageView']);
_paq.push(['enableLinkTracking']);
(function() {
var u="//example.org/";
_paq.push(['setTrackerUrl', u+'piwik.php']);
_paq.push(['setSiteId', '1']);
var d=document, g=d.createElement('script'), s=d.getElementsByTagName('script')[0];
g.type='text/javascript'; g.async=true; g.defer=true; g.src=u+'piwik.js'; s.parentNode.insertBefore(g,s);
})();
</script>
<noscript><p><img src="//example.org/piwik.php?idsite=1&rec=1" style="border:0;" alt="" /></p></noscript>
<!-- End Matomo Code -->
?
Hi,
I have not tested it, but if you want to add the integrity attribute to the <script> tag that loads piwik.js, you can simply add g.setAttribute("integrity","thestring"); in the line between var d=document and g.type=.
Hello, lucas,
can I just include the part like you described or what exactly has to be in the string field?
Hi @Snewi,
thestring would be the SRI hash of the file.
So if you would normally write
<script src="https://example.com/example-framework.js"
integrity="sha384-oqVuAfXRKap7fdgcCY5uykM6+R9GqQ8K/uxy9rx7HNQlGYl1kPzQho1wx4JwY8wC"
crossorigin="anonymous"></script>
it is the sha384- part.
You can calculate the hash with all kinds of tools, e.g.
openssl dgst -sha384 -binary piwik.js | openssl base64 -A
Keep in mind that if you do this and matomo.js changes (because you update Matomo or because you install/update a plugin that modifies matomo.js) it will break.
Ahh ok, does that mean I should better not do it or is there another solution? Do not have desire for all web pages this constantly to correct!
what else do I have to enter in the htaccess to create the hash
<FilesMatch “.(ttf|ttc|otf|eot|woff|woff2|font.css|css|js|gif|png|jpe?g|svg|svgz|ico|webp)$”>
Header set Access-Control-Allow-Origin “*”
Hi,
You don’t have to use SRI. It is mostly intended for embedding Javascript from third-parties you don’t completely trust. (If you should do that in general is another topic)
It has nothing to do with your webserver config. I think that config is only needed to make that website work. But you can just calculate the hash yourself.
I have now calculated a hash over your link and included it in the tracking code like g.setAttribute(“integrity”,“hash”);. Does it bring any advantage and does it make sense to do it this way or not? Which constellation would have to happen exactly so that I would have to enter the hash value again?
Hi,
The point of the hash is to tell the browser: “If this file changed, don’t trust it!”
This means that if some malware on your server changes the matomo.js, browsers won’t load it.*
If some Matomo update changes the matomo.js, browsers won’t load it.
If the matomo.js changes and you want browsers to load the new file, you have to update the hash.
* Assuming this malware can’t just simply also modify the site that is tracked.
ok but then I realize that quickly and can adjust the hash. So it is at least a little bit safer. Can I check afterwards if everything works and is used like this?
Hi,
If the check fails, you can see it in the console of your Browser’s developer tools.
Ok…Thanks for all 
like this? and now?
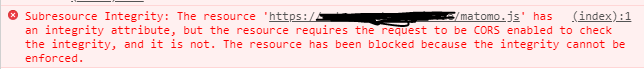
Hi,
It turns out, I was wrong there. You also have to allow CORS for SRI to work.
Note : For subresource-integrity verification of a resource served from an origin other than the document in which it’s embedded, browsers additionally check the resource using Cross-Origin Resource Sharing (CORS), to ensure the origin serving the resource allows it to be shared with the requesting origin.
https://developer.mozilla.org/en-US/docs/Web/Security/Subresource_Integrity
Hi, so my question above about how I need to extend the syntax already in my .htaccess to include sri. Can you help there?
<IfModule mod_headers.c>
<FilesMatch "\.(ttf|ttc|otf|eot|woff|woff2|font.css|css|js|gif|png|jpe?g|svg|svgz|ico|webp|sri)$">
Header set Access-Control-Allow-Origin "*"
</FilesMatch>
</IfModule>